Introduction
Consumer devices are getting more advanced by the day and contain complex software. Device manufacturers need to fix bugs, improve performance and provide new features based on market trends on devices that are already in the field. Device security and data protection are vital aspects too and it is essential to have the latest security updates as and when available, to prevent unauthorized access.

What is OTA?
The term “Over The Air” or OTA for short refers to several methods of updating the software configurations, new features, release versions, bug fixes, Patches etc to a device. The only requirement for the target device is to be connected to the OTA servers via a stable network connection. The connection could be either on WiFi or Ethernet. In fact the term “Over The Air” refers to sending the update package to the target device over wireless internet connection on consumer devices.
OTA updates are specific to the intended target device. An OTA package generated for a specific device/processor/variant can only be applied to that particular device. The procedure is a two-step process. First step is to create the OTA update package from the source code of the targets software release. This package can either be physically copied to the target device or sent over network/internet. The second step is to push the generated update.zip onto the device. The target device initiates download of the Update to a cache or data partition, and its cryptographic signature is verified against existing certificates. The User is then prompted to install the update.
OTA updates on Android
There are two types of OTA updates that can be done on Android.
Seamless A/B OTA updates
This is the latest procedure for running updates on Android Devices in which there are two copies of the working partition (A and B) and thus ensures a workable booting system remains on the disk even during the update. The update is applied on one partition while the system continues to run on the second partition. This also means that if the update fails for any reason, the device can still boot back up using the partition with the older image. There is no requirement for additional space as the required partitions are predefined in the UFS/eMMC. This seamless update method is only supported on the Android OS flavors after Nougat.
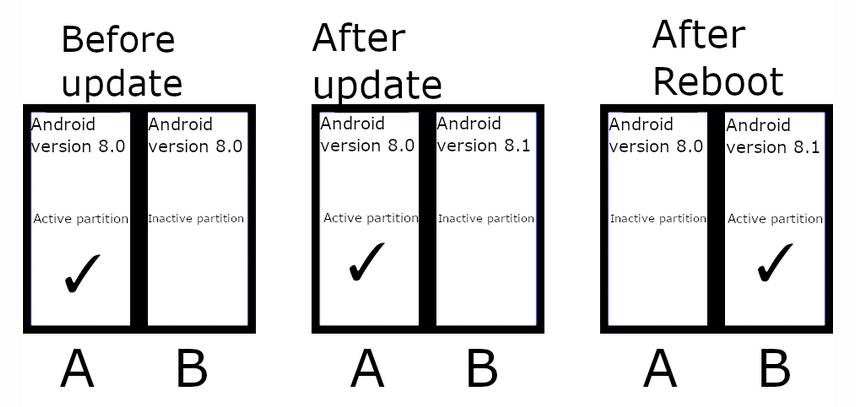 Non Seamless A/B OTA updates
Non Seamless A/B OTA updates
This update method was popular in earlier versions of Android. This works using a recovery partition where the update package is loaded. The recovery partition is a special bootable partition that contains a recovery application that performs the update. The recovery application can access different features without accessing the device's main OS. The device enters into a recovery mode after an update is initiated and the different partitions are updated with the latest updates. This method is not as fail proof as the Seamless update method. If failures like loss of power were to occur during the update in recovery mode, it would result in the device being bricked.
Although it is still possible to use the old method on the latest Android OS, Most OEM’s now have switched to the seamless update OTA method.
Full OTA update vs Incremental OTA update:
Full OTA update is usually used for doing a complete flash of the latest release version. The advantage here is that the device can be on any older build. Also any bugs that may have been caused due to corruption of partitions are also fixed during the update.
Incremental updates are used to do incremental changes on the software. Changes could be related to adding security fixes or bug fixes to the device without losing all the stored data. Incremental update package can only be used on a device that has the old source build used when building the package. To build an incremental update, you need the update package from the old build as well as the current build. The advantage is that the size is significantly lesser than a full OTA package. The disadvantage is that the device needs to be on a specific release/build version for this to work.
A complete procedure of a seamless update on one of our platforms is provided in the following sections.
Seamless A/B OTA Update Procedure on the Snapdragon 660 based Inforce 6560 SBC:
1. The following changes need to be made in the android source code in src/device/qcom/sdm660/BoardConfig.mk and src/device/qcom/sdm660/BoardConfig.mk to enable seamless updates.
diff --git a/BoardConfig.mk b/BoardConfig.mk
index 6215339..e7314f4 100755
--- a/BoardConfig.mk
+++ b/BoardConfig.mk
@@ -42,7 +42,7 @@ AB_OTA_UPDATER := true
# Full A/B partiton update set
# AB_OTA_PARTITIONS := xbl rpm tz hyp pmic modem abl boot keymaster cmnlib cmnlib64 system bluetooth
# Subset A/B partitions for Android-only image update
-AB_OTA_PARTITIONS ?= boot system
+AB_OTA_PARTITIONS ?= boot system vendor
BOARD_BUILD_SYSTEM_ROOT_IMAGE := true
TARGET_NO_RECOVERY := true
BOARD_USES_RECOVERY_AS_BOOT := true
diff --git a/fstab_AB_variant.qcom b/fstab_AB_variant.qcom
index 445245e..a6f03bd 100755
--- a/fstab_AB_variant.qcom
+++ b/fstab_AB_variant.qcom
@@ -8,7 +8,8 @@
# A/B fstab.qcom variant
#<src> <mnt_point> <type> <mnt_flags and options> <fs_mgr_flags>
/dev/block/bootdevice/by-name/system / ext4 ro,barrier=1,discard wait,slotselect,verify
-/dev/block/bootdevice/by-name/userdata /data ext4 nosuid,nodev,barrier=1,noauto_da_alloc,discard,noatime,lazytime wait,check,forceencrypt=footer,crashcheck,quota
+/dev/block/bootdevice/by-name/vendor /vendor ext4 ro,barrier=1,discard wait,slotselect,verify
+/dev/block/bootdevice/by-name/userdata /data ext4 nosuid,nodev,barrier=1,noauto_da_alloc,discard,noatime,lazytime wait,check,encryptable=footer,crashcheck,quota
/devices/soc/c084000.sdhci/mmc_host* /storage/sdcard1 vfat nosuid,nodev wait,voldmanaged=sdcard1:auto,encryptable=footer
/dev/block/bootdevice/by-name/misc /misc emmc defaults defaults
/dev/block/bootdevice/by-name/modem /firmware vfat ro,shortname=lower,uid=1000,gid=1000,dmask=227,fmask=337,context=u:object_r:firmware_file:s0 wait,slotselect
Once this is done, build the binaries using the command “make -j16”.
2. Flash all binaries generated in the previous step on to the
Inforce 6560 SBC.
3. Generate the OTA package using the command 'make otapackage -j8'.
4. Create a python script ‘ota.py’ with the content shared below.
import sys
import zipfile
def main():
if len(sys.argv) != 2:
sys.stderr.write('Use: %s <ota_file.zip>n' % sys.arv[0])
return 1
otazip = zipfile.ZipFile(sys.argv[1], 'r')
payload_info = otazip.getinfo('payload.bin')
payload_offset = payload_info.header_offset + len(payload_info.FileHeader())
payload_size = payload_info.file_size
payload_location = '/data/ota_package/update.zip'
headers = otazip.read('payload_properties.txt')
print ('update_engine_client --update --follow --payload=file://{payload_location}'' --offset={payload_offset} --size={payload_size}'
' --headers="{headers}"').format(**locals())
return 0
if __name__ == '__main__':
sys.exit(main())
5. Copy the generated OTA package in step-3 to a local folder where the python script is placed and rename the package to 'update.zip'
6. Run the command 'python ota.py update.zip' and execute the generated output in device shell(adb). If update is successful then you will see the following.
"[INFO:update_engine_client_android.cc(98)] onPayloadApplicationComplete(ErrorCode::kSuccess (0))"
7. On the next reboot, the
Inforce 6560 device will boot with the new images
8. This step is optional and should be used to create incremental updates. For performing this step the update.zip from the old build and the new build will be required. The above steps can be followed to get the old update (old full OTA update) and new update(latest full OTA update).
$.<androidsrc>/build/make/tools/releasetools/ota_from_target_files -I <path to old update>/old_update.zip <path to new update>/new_update.zip incremental_update.zip # make incremental from the older version
Note:-
- This procedure shows how to create a full/incremental OTA package using the Seamless AB partition method. The delivery and flash of this update via internet or any network can be done by implementing an application to download the required update from a server.
- For an incremental update to be flashed the device must be on a specific older build that was used to create the incremental update.
- Full OTA updates can be flashed to a board regardless of the build version.
Penguin Edge platforms based on
Qualcomm Snapdragon have the Infrastructure to allow OTA updates. Google's OTA infrastructure (Google Play Store services) as seen on Android cell phones for example, will have their own client application that can pull the update files over HTTPS from a server whenever there is an update relevant to that hardware and launch the upgrade application automatically. We would be glad to support you on implementing an update procedure for your IoT devices.

 Non Seamless A/B OTA updates
This update method was popular in earlier versions of Android. This works using a recovery partition where the update package is loaded. The recovery partition is a special bootable partition that contains a recovery application that performs the update. The recovery application can access different features without accessing the device's main OS. The device enters into a recovery mode after an update is initiated and the different partitions are updated with the latest updates. This method is not as fail proof as the Seamless update method. If failures like loss of power were to occur during the update in recovery mode, it would result in the device being bricked.
Although it is still possible to use the old method on the latest Android OS, Most OEM’s now have switched to the seamless update OTA method.
Full OTA update vs Incremental OTA update:
Full OTA update is usually used for doing a complete flash of the latest release version. The advantage here is that the device can be on any older build. Also any bugs that may have been caused due to corruption of partitions are also fixed during the update.
Incremental updates are used to do incremental changes on the software. Changes could be related to adding security fixes or bug fixes to the device without losing all the stored data. Incremental update package can only be used on a device that has the old source build used when building the package. To build an incremental update, you need the update package from the old build as well as the current build. The advantage is that the size is significantly lesser than a full OTA package. The disadvantage is that the device needs to be on a specific release/build version for this to work.
A complete procedure of a seamless update on one of our platforms is provided in the following sections.
Seamless A/B OTA Update Procedure on the Snapdragon 660 based Inforce 6560 SBC:
1. The following changes need to be made in the android source code in src/device/qcom/sdm660/BoardConfig.mk and src/device/qcom/sdm660/BoardConfig.mk to enable seamless updates.
Non Seamless A/B OTA updates
This update method was popular in earlier versions of Android. This works using a recovery partition where the update package is loaded. The recovery partition is a special bootable partition that contains a recovery application that performs the update. The recovery application can access different features without accessing the device's main OS. The device enters into a recovery mode after an update is initiated and the different partitions are updated with the latest updates. This method is not as fail proof as the Seamless update method. If failures like loss of power were to occur during the update in recovery mode, it would result in the device being bricked.
Although it is still possible to use the old method on the latest Android OS, Most OEM’s now have switched to the seamless update OTA method.
Full OTA update vs Incremental OTA update:
Full OTA update is usually used for doing a complete flash of the latest release version. The advantage here is that the device can be on any older build. Also any bugs that may have been caused due to corruption of partitions are also fixed during the update.
Incremental updates are used to do incremental changes on the software. Changes could be related to adding security fixes or bug fixes to the device without losing all the stored data. Incremental update package can only be used on a device that has the old source build used when building the package. To build an incremental update, you need the update package from the old build as well as the current build. The advantage is that the size is significantly lesser than a full OTA package. The disadvantage is that the device needs to be on a specific release/build version for this to work.
A complete procedure of a seamless update on one of our platforms is provided in the following sections.
Seamless A/B OTA Update Procedure on the Snapdragon 660 based Inforce 6560 SBC:
1. The following changes need to be made in the android source code in src/device/qcom/sdm660/BoardConfig.mk and src/device/qcom/sdm660/BoardConfig.mk to enable seamless updates.